Quantifind is delighted to announce the latest enhancements to our risk management tools, rolled out in the second quarter of 2024.
According to the firm, these innovations are designed to assist organisations in managing and mitigating complex risks with unprecedented precision and efficiency. This marks another milestone in its commitment to delivering cutting-edge solutions in the field of risk intelligence.
The firm revealed it was pleased to introduce Graphyte’s new Digital Resource Centre. This online portal provides seamless access to API documentation, detailed definitions of risk factors, and other crucial reference materials. It’s designed to empower their teams to perform initial programmatic screenings using GraphyteAPI effectively, delve into its extensive global catalogue of Data Sources, and interpret adverse signals highlighted within our Risk Factors.
Quantifind’s dynamic risk typologies continue to evolve to address emerging threats in the financial sector. Recently, we have launched a data science project focusing on the broad categories of Insider Trading and Market Manipulation.
By segmenting this risk into three distinct subcategories—Insider Trading, Market Manipulation, and Patent Infringement—the firm has enhanced the accuracy of its risk tagging and the overall precision of our analyses.
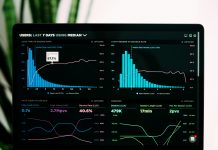
The latest feature from Quantifind is the initial version of the Queue Dashboard, integrated into our Continuous Monitoring solution, GraphyteQueue. This reporting dashboard enables financial institutions to meticulously monitor sanctions, watchlists, and adverse media results.
It’s an essential tool for ensuring comprehensive governance and ongoing visibility into perpetual risk monitoring, said the RegTech firm.
Keep up with all the latest FinTech news here.
Copyright © 2024 FinTech Global